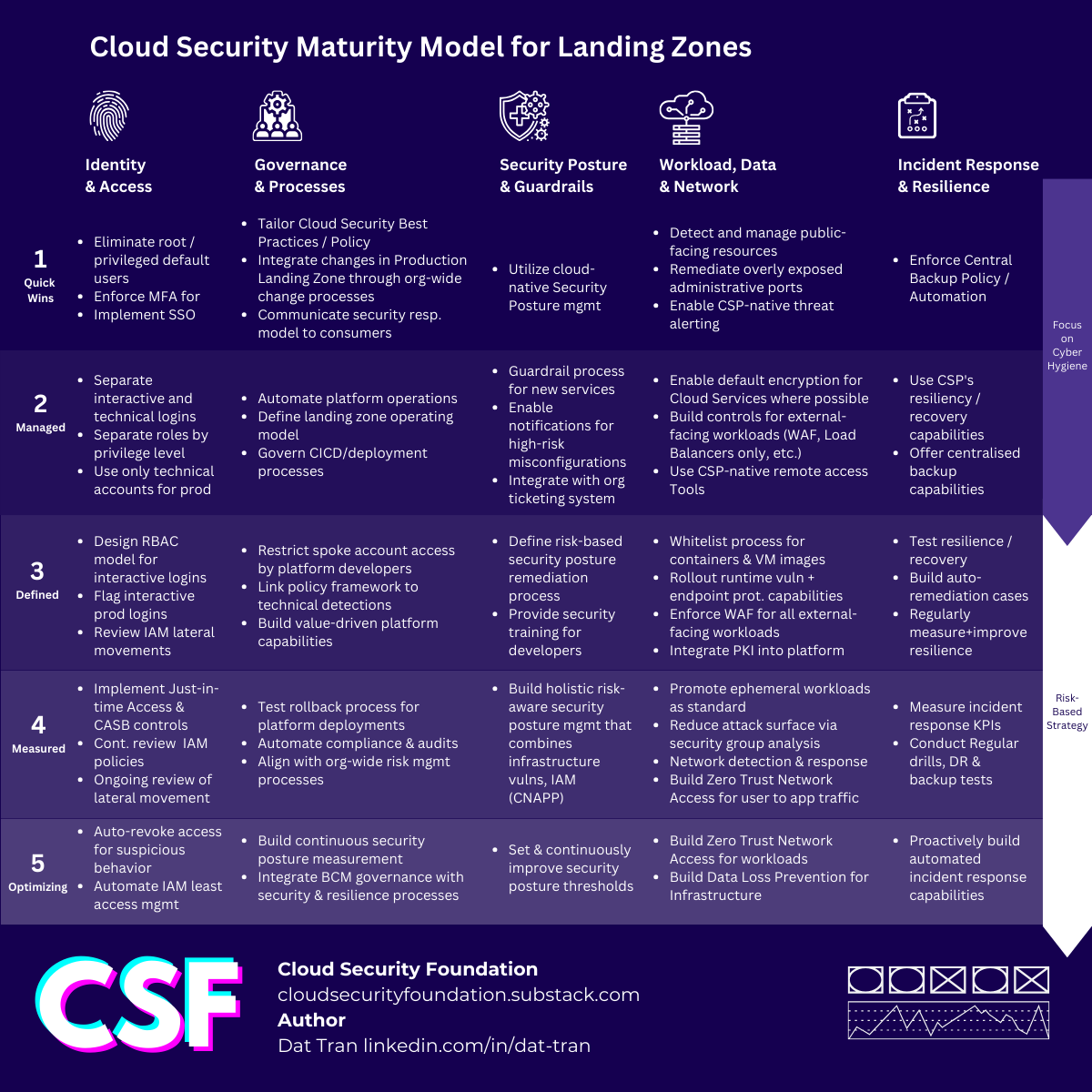
The Cloud Security Maturity Model
Navigating Cloud Security: A Maturity Model for Landing Zones and Beyond
The digital transformation journey has led many enterprises straight into the cloud. Gone are the days when cloud computing was just a buzzword or a distant future. Today, most enterprises have either migrated their workloads into the cloud or are deeply enmeshed in large-scale cloud migration projects. As we navigate this new frontier, the importance of implementing secure landing zones has become glaringly evident—a prerequisite for secure scalability in an increasingly cloud-reliant world.
To understand the gravity of cloud security, one needs to look no further than recent statistics. According to a report by Thales, a staggering 39% of businesses experienced a data breach in their cloud environment last year, marking an increase from 35% in the previous year. Even more concerning, the report reveals that the percentage of businesses storing over 40% of their sensitive data in the cloud has surged by 26%, to a new high of 75%. In light of these startling facts, there's an undeniable need for a robust framework to evaluate and improve your organization's cloud security maturity.
But why landing zones?
As organizations venture deeper into the cloud, most will inevitably establish what is known as a landing zone or a cloud foundation. A landing zone acts as a modular and scalable base that helps organizations tailor their cloud service provider (CSP) services to meet specific business needs. If you're new to the concept, here's why landing zones are integral to secure cloud adoption:
Benefits of a landing zone:
Security and Compliance: Ideally, subscriptions / accounts coming from a landing zone account vending process are secure by design and offer a baselined / hardened secure environment. Furthermore, security can be centralized - offering great visibility into the posture of the entire organisation.
Self-Service Integrations: Landing zone implementations usually offer centrally managed tooling and patterns that deploy infrastructure that allow application teams to use central services. This can be centralized logging and monitoring services to integrations with the ticketing / change management system.
Identity and Access Management: Account management is done centrally (via Single Sign On) to make sure identity level procedures are adhered to - for example identity governance controls (access reviews, user account lifecycle) and extra session protections such the usage of just-in-time privileged access.
Networking: Predetermined networking configurations, firewall rules, and other basic networking parameters to enhance security and to connect directly to the corporate network.
This article aims to provide an opinionated guide to cloud security maturity, particularly for teams focused on landing zone implementations. It serves many audiences, for example:
Landing zone teams looking to validate their security strategies and identify any gaps.
Security teams seeking to evaluate the maturity of existing landing zones.
Executives who wish to gain insights into their organization's overall cloud security posture.
Existing Cloud Security Maturity Models
Several well-known institutions and organizations have attempted to frame the complexities of cloud security into maturity models. Each has its merits, but they also come with limitations, particularly when one is focused on landing zones. Below, we'll briefly review some of the key existing cloud security maturity models.
AWS
AWS provides an opinionated yet actionable maturity model designed to work seamlessly within their ecosystem. While the AWS model is highly effective for organizations solely utilizing AWS services, its AWS-centric focus limits its applicability across multi-cloud environments.
Strengths:
Tailored for AWS architecture.
Provides actionable advice.
Limitations:
Highly AWS-centric; less useful for hybrid or multi-cloud deployments.
SANS Cloud Security Maturity Model
SANS, a trusted source for cybersecurity training and research, offers a Cloud Security Maturity Model that is extensive in its coverage. While the model is comprehensive and useful for gaining an in-depth understanding of cloud security, it sometimes conflates concepts related to landing zones and non-landing zone architectures. This lack of distinction may necessitate another layer of architectural consideration when implementing security measures.
Strengths:
Extremely detailed
Backed by SANS' cybersecurity expertise
Limitations:
Mixes landing zone and non-landing zone concepts and thus may require additional architectural considerations
IANS Cloud Security Maturity Model
IANS offers another thorough Cloud Security Maturity Model. While extremely detailed, it is not easily summarized or visualized on a single page, potentially making it less accessible for quick evaluations and decision-making.
Strengths:
Comprehensive
Covers a wide range of security considerations
Limitations:
Complexity makes it less practical for quick evaluations
Not easily distilled into a one-page summary
All the models mentioned above are excellent resources that offer valuable insights into cloud security. They are, without a doubt, worth exploring in detail. Our goals is to provide a maturity model that focuses on immediate applicability and actionability but is general enough to work for AWS, Azure and GCP.
How to use this model
Here's how you can make the most out of this model:
For Self-Assessment and Roadmap Influence
The model is designed for quick self-assessments, making it easier to pinpoint where you currently stand in terms of cloud security and what steps you need to take next. This can then feed directly into your cloud security roadmap.
Flexibility is Key
Remember, this is a framework, not a strict set of rules. Different companies have different risk profiles and compliance requirements. Use the model as a guide but tailor it according to your unique organizational needs.
Directly Applicable to Engineering and Architecture
One of the model's greatest strengths is its direct applicability. The actionable insights and recommendations can be directly handed over to engineering or solution architecture teams for immediate implementation.
Maturity-based vs risk-based cloud security strategy
Maturity models, including the one we've introduced, can be extremely helpful for organizations to measure where they stand and what steps they need to take for improvement. However, it's crucial to understand that maturity frameworks are often prescriptive and linear, mapping out a series of tasks to achieve. Cyber attackers, on the other hand, operate in a much more dynamic manner. They don’t think in checklists; they think in terms of interconnected systems and opportunities for exploitation. This means relying purely on a maturity-based approach could blind organizations to the real, dynamic risks they face every day.
Our recommendation is a hybrid approach. Use the Cloud Security Maturity Model to establish a good baseline of cyber hygiene—up to at least level 2. Once you have a mature foundation, transition to a more nuanced risk-based approach. This allows for more strategic and effective security planning and implementation, ensuring that you're not just ticking boxes but are genuinely secure.
Thank you for reading - feel free to share on LinkedIn, Threads or X!
In summary, this article offers a practical roadmap for enhancing your cloud security through a maturity model tailored for landing zones. While a maturity-based approach provides a structured start, our long-term vision would be for organisations to transition to a risk-based strategy for long-term resilience and alignment with your specific operational context. Keep an eye out for our upcoming guide on risk-based cloud security to further refine your approach. Thank you for reading, and we wish you success in your cloud security journey.